General Implementation Requirements
We are primarily developing the new version of the software for FIT PLUS. However, we also plan to market and sell the software to other fitness centers in the future. For this reason, we differentiate between:
-
Modules and functions required for the initial go-live (Stage 1), and
-
Functions that are useful for future sales but will only be developed later due to effort and priority (Stage 2)
-
All such future functions and modules are clearly marked with the Stage 2 label in the relevant sections.
Software Deployment Model:
Multi-Tenant Deployment Model with Isolated Databases
Jeydoo uses a single system instance (codebase) to serve multiple clients, while each client has a separate, isolated database. This ensures data security and client-specific configurations without code duplication.
Key Characteristics of Jeydoo's Deployment Model:
-
Single Codebase (Multi-Tenant Application):
All clients run on the same software application instance, reducing maintenance overhead and streamlining updates. -
Isolated Client Databases (Hybrid Isolation):
Each client’s data resides in its own separate database, ensuring data isolation, privacy, and security. -
Modular System with Client-Specific Features:
Shared modules are available to all, while optional custom modules can be developed for specific clients and assigned selectively — without impacting others. -
Three Access Panels:
-
Global Admin Panel (for internal Super Admins)
-
Client Management Panel (for clients managing their operations)
-
Employee Booking Panel (for staff to log time)
-
This approach ensures:
✅ 100% data separation
✅ Full compliance with legal and data protection regulations
Listing Views:
-
All listing views include a search function that searches across all available columns.
-
Each listing also includes pagination at the bottom for easier navigation through large datasets.
Hosting
The hoster must be a company based in the EU, preferably in Germany, that is certified according to the usual standards. The required certifications include ISO 27001 for information security management, ISO 9001 for quality management and ISO 14001 for environmental management. These certifications ensure that the hoster maintains high standards in terms of security, quality and environmental awareness.
Based on latest discussion, we will host on Hetzner as our Hosting Company
Security
Security is not an afterthought, but an essential component of every modern web application. In times of growing cyber threats, increasing data protection regulations (such as GDPR) and increasing frequency of attacks on digital systems, it is essential that development teams consider cyber security from the outset. All aspects of security are taken into account.
Data protection
As personal data is processed in payroll accounting, the strict requirements of the GDPR apply here. Deletion and anonymization periods must be adjustable. More on this in the Admin & Settings section.
Revision security
Each part of the software must be designed to be audit-proof. This means that every change—whether related to data or system configuration—must be logged and securely archived. These logs must be unalterable and tamper-proof to ensure complete transparency and traceability at all times.
The descriptions of the individual software modules will specify the exact measures implemented to meet these revision security requirements.
Additionally, revision reports will be introduced in Stage 2 to provide structured overviews of all logged changes.
Stage 1:
The system needs to log and archive every change (audit-proof design) so that nothing is lost or altered, but no formal revision reports need to be generated yet.
Stage 2:
The Revision Report feature will be implemented—this is where those logged changes will be made visible, structured, and accessible in report format for auditing, review, or compliance needs.
Stephan/Silvan to study & research on the exact expectation of this topic
Time recording
Working hours are an important basis for employee payroll accounting. We differentiate between the following for the calculations:
- Working time owed: The contractually agreed working time in hours
- Hours worked: The actual hours worked in the payroll month
There are basically two different ways of booking time:
- Booked times: Booked times are recorded by the employee clocking in and out at the start and end of work. Breaks are also clocked in and out.
- Manual times: However, times that cannot be stamped on site by the employee are also relevant for subsequent calculations. Such as vocational school, sick leave, vacation. These times are recorded in "Manual times". The exact definition can be found in the "Time types" chapter.
Area: Time booking (on site)
On-site time booking takes place on a PC. There we provide an input mask with which the employee logs in to book attendances and breaks.
Login
There are two ways to log in.
1. Login via employee chip wristband
Each employee has a physical employee chip that is provided with their employee ID. A reader that can read this chip is connected to the PC. Based on his ID and the status "active" in the user master data, we log the employee in and show him some information and four buttons for time bookings.
The standard for the chip wristband is:
RFID chip wristband - Mifare 1K, 4 bytes - quasi 10 digits
Silvan/Stephan will bring us the above hardware during September for hands-on testing.
Still in the midst of discussing the following :
- What is the best login method that is fast, efficiency and reduce login error
- example: if employee A scan wristband, and doesn't choose a login button for [ x ], the system will automatically logout, and employee B will not make his selection during login session of Employee A
- If employee A scans his/her wristband, does he/she enters Dashboard / Login panel directly
- What if employee forgot to bring his/her wristband ?
- Do we implement 2-factor authentication ?
- Nothing is being finalised yet during our earlier discussion
2. Login via username & password
This is a classic login with a user name and password. This should only be used if the employee has forgotten or lost their chip at home. Later on, we will also need it if customers do not use employee chip wristbands.
Internal discussion as to whether two-factor authentication makes sense or whether we should choose a different approach for the login. For security reasons, it would also be conceivable to decouple the login from the actual app and make it available locally. Or limiting the number of logins to a number that is released again by the Center Admin after use.
Logout
If the user clicks one of the four booking buttons (see below), we display a short text message that the time has been successfully booked and log the user out directly.
If the user is inactive, the user is automatically logged out after 10 seconds.
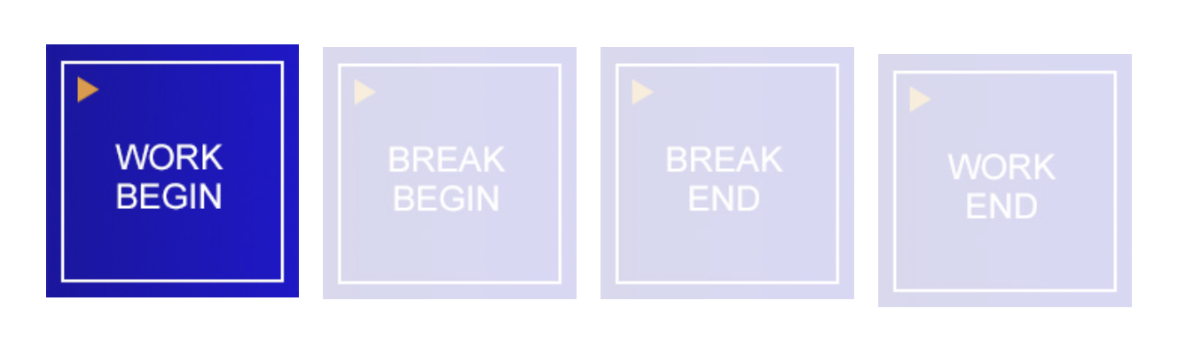
Buttons Time bookings
To avoid errors when making bookings, only the buttons that are logically possible are active.
...is active if there is no open work entry beforehand.
Button 2: break begin
...is active if there is a time stamp today that has a work start but no work end. Please note that it is possible for employees to work twice in one day. The latest open time stamp is therefore used for the check.
Button 3: break end
… is only active if there is an active pause.
Button 4: work end
… is only active if there is a running time stamp for the start of work and no break is open.
Example Scenario :
If an employee clicks on [ Work Begin ]. The next Login, [ Break Begin ] and [ Work End ] button are active.
If an employee clicks on [ Break Begin ] on the next login, only [ Break End ] button will be active.
If an employee clicks on [ Break End ] after coming back from his/her breaks, [ Work End ] button will be active.
Employee needs to clicks [ Work End ] every time he/she leaves the workplace.
In case any error happens on the above workflow, example: employee clicks on [ Work Begin ] but didn't click on [ Work End ] within the same day OR he/she clicks on [ Breaks Begin ] but didn't end the breaks later.
System will automatically logs them out after midnight, an error report will be generated.
Still need finalization/confirmation on the above workflow.
Timestamp format
An important aspect is that all time stamps are saved in the correct UTC format. The background to this is that the correct distinction can be made in the subsequent calculation of salaries as to when the employee worked.